Ransomware 101: a step by step breakdown
Ransomware is back in the headlines, which makes this research paper's clear and useful analysis of how it works a valuable primer for business leaders
This week’s JBS attack saw the latest case of corporate cyber attack take over headlines all over the world, and it culminates a year that has seen digital ransomware activity rise to new heights during the pandemic. This recent spike, however, is but a continuation of a recent trend. Indeed, in both 2018 and 2019 ransomware insurance claims increased by over 100%. These attacks are not only more frequent, they are also more audacious in their demands. Back in 2019, the typical ransom demand averaged less than $10,000. This figure has been increasing alongside the success of the actors, and it culminated with CWT’s $4.5M payout in 2020 (followed closely by Colonial Pipeline's rumored $4.4M payout to restore its operations last month).
Figure 1: Propensity to be hit by ransomware across different industries (Source: Sophos)
Retail and education organizations are still the most common targets, notes one recent report, but ransomware agents, according to another study, are becoming more selective about their targets. The pandemic saw a rise in healthcare sector attacks, for example, and manufacturing and government are increasing favorites given their sensitivity to downtime and public impact, respectively. Ransomware is also beginning to shift to blended “extortion-and-ransomware” attacks, notes the first report:
Here, in addition to encrypting local files, the ransomware steals copies of sensitive files and the gang threatens to make the documents public unless the ransom is paid. When the ransom has not been paid, some firms have seen their data auctioned on the dark web with prices ranging from $5,000 to over $20 million. According to IBM, the ransomware gangs are targeting the ransomware amounts to the specific firm. Known ransoms ranges from 0.08 percent of annual revenues to as high as 9.1 percent.
As common as ransomware is, the exact nature of the threat is often not fully understood outside the technical community. Yet understanding both the nature of ransomware attacks and their constituent elements is a priority for leaders outside of the cybersecurity function. Unfortunately, most of the general press discussions of ransomware are, understandably, superficial, and most of the academic literature is too complex for non-technical audiences. However, a recent survey of the subject by Masoudeh Keshavarzi and Hamid Reza Ghaffary (Islamic Azad University) provides a thorough and helpful overview of what ransomware is and how it works.
Ransomware taxonomy
Ransomware, as its name suggests, is a species of malicious software (malware) that takes a user's resources hostage and demands some sort of payment in exchange for the release of the resources. It's generally accepted that the first ransomware attack was the AIDS Trojan virus distributed via diskettes in the late 1980s. Its malicious code encrypted user files and then demanded $189 for their release. AIDS Trojan was simple, technically, and flawed in many ways. In the decades since its appearance, the ransomware ecosystem and technologies have evolved tremendously. Indeed, it may be the most lucrative form of cybercrime today.
Figure 2: The authors’ proposed taxonomy of the extortion-based attacks (Source: Authors)
Ransomware itself is a type of scareware, which is malware whose basic mechanism is the creation of fear in the affected party in order to elicit a desired action. The authors divide scareware into three categories:
Class 1: Rogue security software
Rogue security software is one of the most known and common scareware types. Rogue software typically infects a machine and pretends to have access to all of its data or to be able to destroy it in some way. This type of ransomware is a kind of "cyber-bluff" [my term] that hopes a user will pay up for fear of data loss or data discovery by outside parties. As the authors note, the main difference "between rogue utility and classical ransomware is that rogue software does not typically deny access to the resources and damage the victim device."
Class 2: Ransomware
True ransomware is distinguished by the fact that it does actually take control of a target machine or network and prevents users from accessing them until the ransom is paid. Generally speaking, ransomware comes in two forms.
The first form is denial of data resources (DoDR), in which the ransomware blocks access to the data resources and requires victims to pay a ransom to regain access to their data. Crypto-ransomware is the most common form of ransomware, and modern forms do effectively what the AIDS Trojan virus did back in the 1980s: they stop you from accessing your machine and its contents until you pay the ransom. Other examples of DoDR ransomware include WannaCry, Petya, PetWrap, NotPetya, AnonPop, Ordinypt, and MBR-ONI.
The second type of ransomware locks out resources but leaves the user data intact. Data may seem inaccessible at first glance, note the authors, "but the main difference with the previous group (i.e., DoDR) is that the data will not be tampered with or destroyed." Therefore, "it makes DoNR less effective at extorting victims compared with its counterpart."
The most well-known version of this second class of ransomware is locker-ransomware that generally infects a mobile, IoT or cloud device and extorts a payment to unlock it. Once infected, these attacks can compromise operating systems, applications, services, user interfaces, and other utilities. For example, note the authors, the Trojan.Ransomlock.G virus "locks the user’s screen and displays a full-screen ransom note that covers the entire desktop."
Class 3: Leakware
The third type of ransomware is known as leakware or doxware. This class is an "evolution" of cyber blackmail since the threat is the release of sensitive or secret information into the public domain. Doxware "utilizes the mechanisms of spyware and info stealer, and in some cases, it combines them with ransomware methodologies, such as cryptography or locking." Of course, doxware is unique in that rather than making data unreachable, it makes the data reachable to anyone unless the victim pays up. Leakware may be the most dangerous of all the three classes, note the authors:
...Leakware is more dangerous than all breeds of ransomware, as backup strategies cannot mitigate the damage caused by it. What makes the Leakware worse and more persistent than other extortion-based attacks is that even if the victim pays the ransom, she/he may still be threatened because a copy of the data is in the hands of adversaries.
Ransomware progression
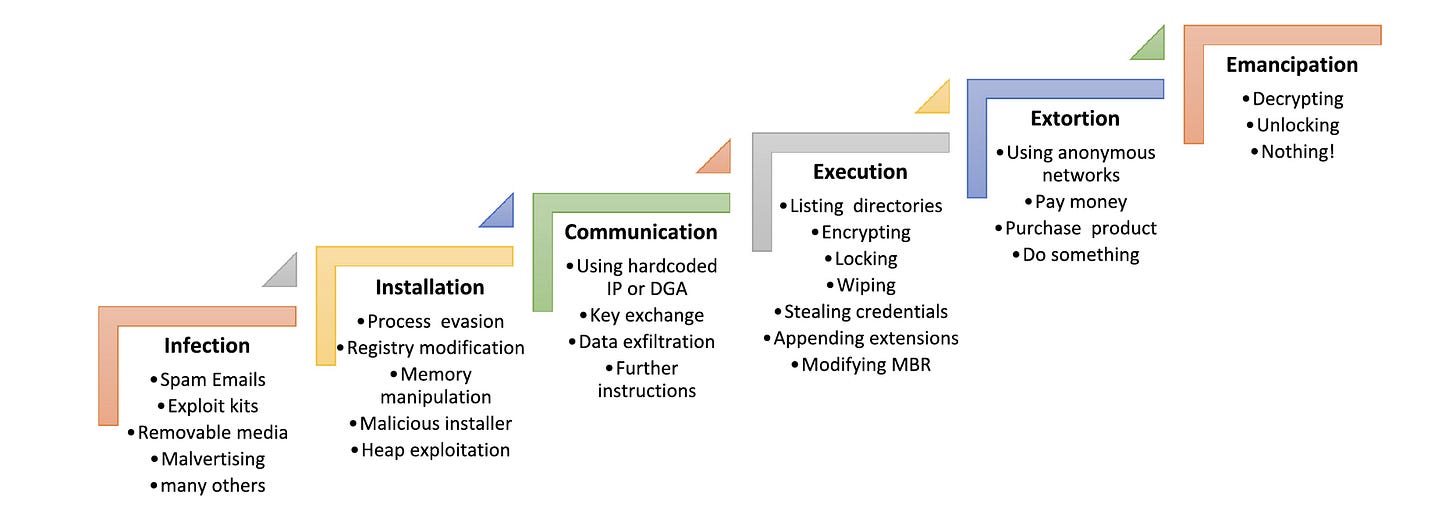
After outlining the three classes of ransomware, the researchers move to the most useful section of their paper: the sequential analysis of a ransomware attack.
Figure 3: The authors’ proposed attack chain for all types of ransomware (Source: Authors)
Phase 1: Infection
All ransomware attacks start the moment the bad code enters a victim's machine or network. Although there are many ways to get the code into a victim's machine, most ransomware attacks employ spam phishing or what are known as exploit kits (basically a set of pre-determined software actions). The spam emails "contain either malicious attachments (e.g., a Microsoft Office document inclusive of macro, a PDF file with JavaScript) or a link to a compromised website." Some methods need a user to click to download the ransomware code, but some recent attacks do not.
As noted, the first known ransomware, AIDS Trojan, used infected diskettes to deliver its malware. But with "the extension of botnets and their prosperity in sending massive amounts of spam emails, the rate of adopting spam emails has been raised for distributing malware to as many users as possible." Moreover, new variants such as "cryptoworms" have emerged that act more like true viruses: they self-propagate without the need for any user activity and spread with amazing efficiency. As one 2016 ransomware report noted:
When Locky, which used infected Word files to spread ransomware, was brand new, there were reportedly 100,000 new infections per day; at one point there were between one to five new endpoint infections per second. If only one-fourth of the daily 100,000 victims paid the ransom of .5 bitcoins, which is about $213 today, then the cyberthugs were pulling in over $5 million per day.
Phase 2: Installation
"After the malcode is delivered to the victim machine through aforementioned vectors, ransomware enters the installation phase." At this point, ransomware must "install itself on the system and take control of the device, without attracting the attention of security software." In order to do this, ransomware has many techniques. For example, "process hollowing" and "process doppelganging" both allow malware to hide. In the former technique malicious code is injected into code, say a normal Windows routine. The latter is "a novel and very sneaky technique" for cross-process injection that inserts bad code into a small section of good code. The good code hides the bad code from security software, and so it runs undetected.
Phase 3: Communication
Once the installation of ransomware is completed, it starts to collect the victim’s specifics. This information, "which is later exfiltrated, includes the victim’s IP address, location, operating system, version of browser and its plugins, security tools installed on the device, and so on." Some ransomware codes need to communicate with their command and control (C&C or C2) server in this phase. This communication "is accomplished mostly with the intention of exchanging encryption key and receiving required instructions to keep on attacking."
Phase 4: Execution
In Crypto-Ransomware and Wiper attacks, an additional step is required: locating the most important files that should be attacked. The search process "can be as simple as seeking files with specific extensions to more complex procedures that consider the last accessed files or the entropy of the files." After scanning all directories, the malicious operation begins. Typically, "only files that are matched with predefined extensions (or conditions) are encrypted or manipulated." While all this is going on, many ransomware tools can also steal credential/login information. For example, "HDDCryptor leverages a utility tool for extracting credentials from the last session to reach the previously accessed network drives, which are not currently mounted." Once execution is complete, many ransomware packages install their own boot software and display the dreaded ransom note.
Phase 5: Extortion
Unlike many other types of malware, ransomware must alert the victim of its presence and provide further instructions. True ransomware does not seek to steal data and sell it to a third party, so it must collect compensation from the victim. Thus, in Phase 5 "a ransom note is displayed typically in the language based on the geolocation of the victim’s machine IP address (in the forms of background image, HTML file, text file, and so on)." In many ransomware attacks, the content of the ransom note is hardcoded in the malware binary itself, but other types may download it from the C&C server during Phase 3.
As with all fear-based attacks, social engineering techniques are commonly used in Phase 5 to persuade victims to pay. To do this, note the authors, "many Crypto-Ransomware and Wiper-Ransomware families specify a deadline that if the payment is not made by that time, the private key (necessary key for decryption) will be permanently destroyed or the requested amount will be doubled."
It seems quaint now that AIDS Trojan asked for payment via international money order or cashier’s check sent to a P.O. Box in Panama. Today, of course, attackers prefer an anonymous payment method. Indeed, the arrival of cryptocurrencies is thought to be a main driver in the increase in ransomware, since they eliminated one of the riskiest steps in the old business model. Indeed, notes consultancy Marsh, “in the first half of 2020, average ransomware payments increased by 60%, with bitcoin used for most payments.”
As efficient as collecting payment has become, money is no longer the only motivator of ransomware attacks:
Many ransomware attacks are emerging for political purposes, spying, sabotaging, or camouflaging other types of malware. For instance, Unit 42 research group from Palo Alto Networks has spotted a new strain of ransomware called RanRan with a political motive instead of a monetary payment. It targets Middle Eastern organizations and extorts them by forcing victims to post a seditious political statement against a Middle Eastern political leader (the victim’s country leader). Rensenware is another example of Crypto-Ransomware with non-monetary incentive that looks more like a joke. In order to decrypt files, it asks the victim to get needed score in the TH12 ∼ Undefined Fantastic Object, a shooting game specified in the ransom note.
Phase 6: Emancipation
The authors note wryly that even in the ransomware game, survival depends on keeping your promises, so once payment is made the cyber hostages must be released. Some recovery methods are straightforward. For example, in "the Crypto-Ransomware attacks, after paying the ransom, a link to a victim-specific decryption tool is sent to the infected user." Other recovery methods are more complex. While it may be hard to believe, some ransomware pros happily provide online chat support to victims post-payment to ensure that the latter can recover as promised.
Ransomware enablers
Throughout all six phases, several elements of today's technology landscape made ransomware possible and the authors thus highlight some of the most relevant items on this list.
Cryptography
Ransomware employs an assortment of techniques to block users’ access to their resource. The most common and interesting techniques is cryptography. Traditionally, cryptography is a serviceable technology to information security on the fly. It is defensive in nature, and provides privacy, authentication, and security to users. But this technology can be misused against security.
Social engineering
Social engineering is employed in ransomware attacks by stimulating user’s emotions, such as curiosity, fear, urgency, and so on to perform an action. Given the progress and complexity of security measures, it is possible to say that social engineering techniques are the easiest way to propagate malware. As mentioned before, one of the major vectors of pollution which requires user interaction is spam email. Most ransomware attacks are initiated by enticing victims into visiting a malicious webpage or opening an infected attachment in the phishing email through social engineering techniques.
Many ransom notes contain countdown timer, which means that criminal groups will increase the amount of ransom exponentially or, in some cases, will eliminate a number of files forever after the expiry date. In addition, the specified deadline will lead to discouraging victims from seeking therapeutic solutions and making mistakes in their decision-making. These menacing tricks will be more effective in companies and organizations such as hospitals, where ‘‘time’’ plays a crucial role, so that most victims consider themselves forced to pay ransom. WannaCry, SamSam, Defray, and BitPaymer are examples of this case.
Botnets
Spam botnets are one of the main pillars of cybercrime attacks on a large scale. Given that spam phishing email is one of the major infection vectors, the issue of spam sending botnets must be considered as one of the key actors involved in distributing ransomware. In brief, botnets are a network of hundreds to millions of compromised machines so-called zombie under the command of a botmaster. Botnet-based spam campaigns by programming a large number of distributed bots are able to transmit tens of thousands of spam emails to many users in a short time interval. Botnets have always played a primary role in many cyberattacks, including DDoS, banking Trojans, money mule spamming, ransomware, and crypto miners.
Anonymous networks
There are many reasons for employing anonymous network technology in cybercrime. The most prominent of them is the lack of traceability by law enforcement agencies and authorities. The use of anonymity in communications neutralizes the embedded blacklisting strategies in many security tools. This technology is clearly evident in the three phases (i.e., communication, extortion, and emancipation)...many ransomware families leverage a variety of anonymous networks like Tor and I2P to communicate with [the] C&C server for bypassing network traffic inspections.
Domain generation algorithms (DGAs)
Ransomware campaigns leverage various techniques to bypass security systems to prevent their C&C servers from taking down. This is where DGAs come into play as a secret mechanism for communicating with C&C servers. Applying this technology will make it harder to turn off C&C servers at least until the algorithm is completely reverse engineered.
Ransomware as a Service
Over the past few years, ransomware threats have soared dramatically. One of the reasons for this progress is the concept of ransomware-as-a-service, called RaaS. The emergence of RaaS platforms has equipped any users with malevolent intent with tools for creating their own ransomware variants, even sans previous knowledge. In this way, the main authors of ransomware focus on the development and promotion of malicious code and delegate its propagation to affiliates. By dint of easy access to RaaS, cybercriminals can comfortably move to the website providing RaaS and with little effort build their own ransomware variant. The RaaS provider groups pocket a portion of ransom revenue for every successful infection.
Defending Against Ransomware
Having thoroughly analyzed ransomware and its principal enabling technologies, the authors then note the various defense mechanisms possible at each stage. I summarize each briefly below.
Defend at the infection phase
The most operative strategy for circumventing any attack relies on preventing that in the first place. Understanding how various strains of ransomware infect devices is crucial for counteract such threats. Because most ransomware species are being delivered through malicious attachments or links included in phishing spam emails, analyzing, and protecting emails is an essential subject.
Defend at the installation phase
Regardless of what the infection vector is, the malicious payload is delivered to the victim’s system, either as an executable binary or as a script or macros embedded in the file, and needs to be installed to continue the attack process. The best defense strategies in this stage are file and process monitoring at the endpoint.
Defend at the communication phase
Many cyberattacks need to communicate with their command center in order to complete the attack process, propagate and infect more devices, or exfiltrate the victim’s information. Ransomware is no exception. In many of ransomware families employing asymmetric cryptography, since the key pair is generated only after a successful connection with [the] C&C server, if communication is disturbed by security measures or never established, the attack will not arrive at the destructive execution phase.
Defend at the execution phase
Although the defense in the execution phase is somewhat late, it may be argued that the most practical defense solutions for previously unknown ransomware families are deployed in this stage. DoDR ransomware requires files’ read and write operations to encrypt or tamper their content. One of the most effective and commonly used methods for defending ransomware in the execution phase is to monitor file system activity by various approaches...also, in Crypto-Ransomware class, a defense strategy is to take advantage flaws in the design and implementation of cryptography algorithms. In the case of using symmetric cryptography, since the key remains in the victim’s machine until the user is online and the key is sent back to the C&C server, memory forensic tools can be leveraged for memory dump.
Defend at the extortion phase
The gangs behind ransomware attacks not only look for secure and untraceable, but also easy payment and exchange methods for victims. The most prominent digital currency used in cybercrime is Bitcoin. However, the footprint of Monero has also been seen in Internet attacks, especially crypto miners. Assenting victims to pay ransom demands can assist to fortify hackers behind ransomware, whilst there is no guarantee of recovering data and repeating this attack on the same victim. While many of the destructive operations have been carried out before the extortion phase and access to resources has been prevented, this stage can also provide an opportunity for defense.
Defend at the emancipation phase
Identifying ransomware family via information included in the ransom note left on the victim’s machine or by analysis methods can be useful for unlocking or decrypting affected files. Because some of ransomware variants already have been discovered by third-party security companies and released their countermeasures. Therefore, all studies that have identified ransomware families can also be used at this phase...Because some of ransomware families have begun to target backup files as a part of their execution phase. Inspecting the accuracy of backups and recovering files from them in a testbed should be considered as a part of backup plan.
Conclusions
Ransomware is already an expensive proposition to victims. Indeed, about 75% of attacked entities do refuse to pay and as a result, suffer losses (on average) of about $623K per occurrence. Paradoxically, firms that do pay end up paying almost twice as much when all is said and done to return to their pre-attack state. This may sound counterintuitive but a recent report explains this outcome:
Well even if you pay the ransom, you still need to do a lot of work to restore the data. In fact, the costs to recover the data and get things back to normal are likely to be the same whether you get the data back from the criminals or from your backups. But if you pay the ransom, you’ve got another big cost on top.
These costs increase as local labor costs increase, notes the report, with Austria having the highest recovery costs in the world:
Figure 4: Average ransomware remediation cost by country (Source: Sophos)
Given that about one of four companies does pay some or all of the ransom, as well as the rise of anonymous payment mechanisms — not to mention RaaS — it's reasonable for most executives to expect ransomware attacks to continue in the near future. It has become, simply put, a cybercriminal’s most effective business model. Indeed, with average ransomware recovery costs quickly approaching $2M globally, there is a need for a clearer understanding of how these attacks move across their lifecycle as well as the technical and human phenomena that enable that progression. Moreover, while there are many technical issues that enable ransomware, the social engineering aspects, as I noted in a recent post, are sorely lacking in academic and practitioner focus. The taxonomy and sequential model provided in this research make a valuable contribution to those ends, and it would be useful to see this level of analysis and understanding inform the general business literature on this issue, which so often tends to focus on ransom amounts and worst-case scenarios rather than the tactical mechanics of, and solutions to, this growing problem.
The Research
M. Keshavarzi and H. R. Ghaffary. I2CE3: A dedicated and separated attack chain for ransomware offenses as the most infamous cyber extortion. Computer Science Review, Volume 36, 2020, 100233, ISSN 1574-0137. https://doi.org/10.1016/j.cosrev.2020.100233